A month ago, something happened that brought my professional world crashing into my personal life: my car was stolen from my driveway in the dead of night. As a cybersecurity journalist with nearly two decades of experience writing about car hacking, I’ve always been aware of the threats, yet I still fell victim to them. This isn’t just my story; it’s a stark reminder of the evolving methods of car theft and the vulnerabilities in modern vehicle security systems, particularly concerning keyless ignition and OBD2 (On-Board Diagnostics) tools.
While specifying my car as a Mercedes-Benz might seem brand-centric, it’s crucial because the make and model are directly relevant to how it was stolen. It also allowed me to engage in a vital conversation with Mercedes about vehicle security, insights from which are included here. For context, this Mercedes was the nicest car I had ever owned – proving that these sophisticated theft methods target everyday vehicles, not just luxury models.
For years, I’ve reported on car hacking, even interviewing cybersecurity experts like Charlie Miller. Like many, I understood the risks intellectually but felt a sense of detachment, a misguided belief that “it won’t happen to me.” This incident shattered that illusion, making me acutely aware of the reality faced by hundreds of thousands of car theft victims annually.
In the UK alone, car theft statistics are alarming. Recent DVLA figures indicate a car is stolen approximately every eight minutes. Office of National Statistics data reveals a staggering 397,264 cars were stolen in England and Wales between October 2022 and September 2023. Land Rover tops the list of most stolen vehicles, followed by Mercedes and Ford. Recovery rates are dismal, with most sources suggesting less than 20% of stolen vehicles are ever recovered.
This grim picture prompts a critical question: how are these vehicles vanishing without a trace, often with no signs of forced entry? The answer, increasingly, lies in sophisticated methods exploiting keyless ignition systems and the vulnerabilities accessible through a car’s OBD2 port.
The Silent Theft: Keyless Entry and Suspicions of Hacking
My car was a Mercedes-Benz GLC 220 AMG Line Premium D, equipped with keyless entry and start. The detective investigating my case informed me that six similar high-value cars were stolen within a mile radius over just two nights. Law enforcement suspects an organized crime group, likely travelling from major cities, was responsible.
Finding my driveway empty one February morning was a shock. Both car keys were exactly where they should be inside my house. There was no broken glass, no sign of forced entry on our secluded driveway. The realization dawned quickly: my car had likely been “hacked.” But was it truly hacking in the traditional sense?
Graham Cluley, from the Smashing Security podcast, confirmed my suspicion: “In its broadest sense, hacking is gaining unauthorized access, and the criminals who stole your car did just that by exploiting a flaw in its entry system.”
David Rogers, CEO of Copper Horse, a connected car security specialist, concurred: “It’s almost certainly car hacking.” Most experts I consulted agreed.
However, Adam Pilton, a former police officer and now cybersecurity consultant at CyberSmart, offered a nuanced perspective. “While ‘car hacking’ might suggest a complex attack, given the multiple thefts in the area, a relay attack is more probable – a simpler yet highly effective method.” This raises a crucial point: is a relay attack a form of hacking?
Ivan Reedman, director of secure engineering at IOActive, injected a dose of reality. “If we define hacking as gaining unauthorized access to data in a system, then this isn’t technically a hack. The criminals gained access to the car, but not necessarily data. I’d argue it’s theft facilitated by technology, rather than pure hacking.”
Relay Attacks: The Gateway to Keyless Car Theft
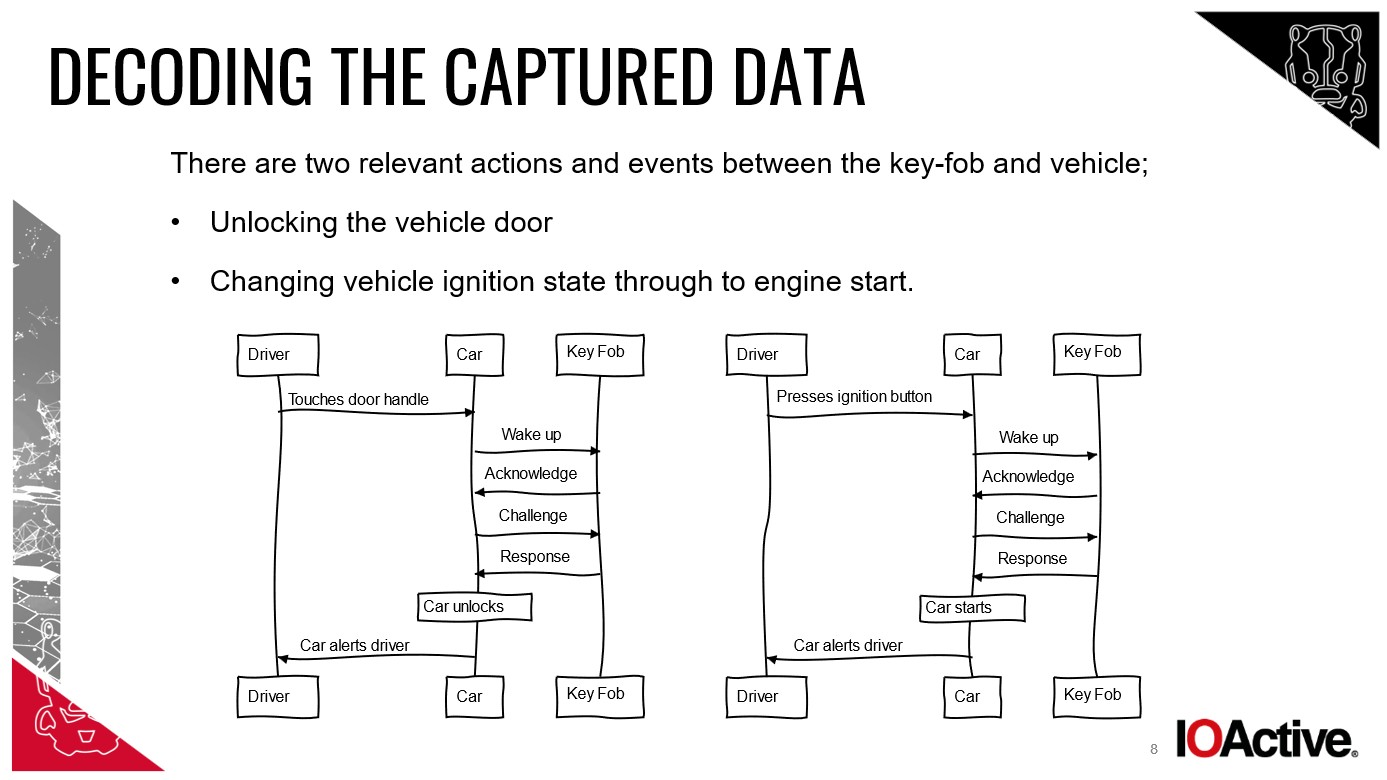
Despite differing opinions on terminology, the cybersecurity experts I spoke with unanimously agreed on the likely method: a relay attack. My Mercedes had ‘Passive Entry Passive Start’ (PEPS). This meant as long as the key was nearby, I could unlock and start the car without pressing any buttons.
Understanding the Communication: How keyless entry systems normally function between the key fob, car, and driver.
Chris Pritchard, a principal adversarial engineer at Lares, explained: “Thieves use a tool to relay the signal between your key fob and the car. The car is tricked into thinking the key is close, unlocking the doors.”
William Wright, CEO at Closed Door Security, elaborated: “Two devices are typically used. One, placed near your house, intercepts the key fob’s signal, even through walls. The other, positioned by the car, relays this signal, mimicking the key’s presence.”
Relay devices need only be within 10-15 meters of the key and can operate in as little as 30 seconds. Reedman highlighted the simplicity: “Relay attacks are among the easiest, requiring minimal technical skill or secret knowledge.” He demonstrated this to the BBC using basic components like an audio amplifier and copper wire, unlocking and driving off in a Mercedes AMG belonging to a BBC producer.
But gaining entry and starting the engine via a relay attack is just the first step. How do thieves keep driving once the car realizes the key isn’t present?
Reedman clarified, “Once started, most vehicles warn that the key isn’t present but won’t shut off the engine. The engine will run until turned off. It’s after this point that the criminals typically leverage the OBD2 port.”
Cluley added, “A car won’t stop mid-drive if it loses key signal – that would be dangerous if the key battery died, for example. But restarting might be prevented.” This is where the OBD2 tool becomes indispensable for car thieves.
OBD2 Tools: The Key to Long-Term Control and Reprogramming
Access through a relay attack gets thieves into the car and allows them to drive away initially. However, to gain persistent control and potentially reprogram the vehicle, they need to interface with the car’s computer system. This is achieved through the OBD2 port and readily available OBD2 programming tools.
“Access to the OBD will trigger the car into starting by using other devices,” Rogers explained. “Once the car is fooled into thinking the driver has legitimate access, there’s no reason to prevent driving.”
Pritchard detailed the OBD2 port’s location and function: “It’s a port, usually under the steering wheel on the right. Mechanics use it for diagnostics and resetting warning lights.” Crucially, it’s also used for key programming. “When my Audi was stolen for an armed robbery, they programmed a new key using an OBD tool. Something similar likely happened in your case.”
This brings us to the core of the issue: Can A Keyless Ignition Be Programmed With An Obd2 Tool? Absolutely. OBD2 tools are designed for legitimate purposes – diagnostics, maintenance, and yes, key programming. However, these tools, when in the wrong hands, become powerful instruments for vehicle theft.
Modern vehicles rely heavily on electronic control units (ECUs) that manage everything from engine performance to security systems. The OBD2 port provides direct access to these systems. Thieves exploit this access to bypass security measures and program new keys, effectively cloning a key or adding a completely new one, even without the original key present.
While key cloning might seem like a sophisticated method, experts suggest that using OBD2 tools to program a new key is often a simpler and more direct approach for thieves after a relay attack. Reedman dismissed the idea of key cloning in my case, suggesting OBD2 programming is more likely.
Flipper Zero and Key Cloning: Less Likely Culprits in This Scenario
Initially, after sharing my experience on social media, some experts suggested a Flipper Zero attack. The Flipper Zero is a multi-tool device capable of various wireless manipulations, including capturing and replaying signals from key fobs in some older car models.
The Flipper Zero device has been controversially linked to the rise in auto theft, particularly by the Canadian government.
However, the experts I interviewed for this article deemed Flipper Zero involvement in my car theft “highly improbable.” Pritchard stated, “As much as the Canadian government blames Flipper Zero for rising car theft, this wasn’t a Flipper attack.” He referred to Canada’s ban on Flipper Zero devices, highlighting the device’s capabilities to exploit vulnerabilities, but emphasizing it’s not the primary tool for sophisticated relay and OBD2-based thefts of modern cars like mine.
While Flipper Zero can unlock some older cars or replicate signals, it’s less effective against modern vehicles with rolling codes and more advanced security. For sophisticated theft rings targeting newer cars, relay attacks combined with OBD2 key programming are far more efficient and reliable methods.
The Accessibility of Car Theft Tools and the Perpetrators
Having established how my car was likely stolen – relay attack followed by OBD2 key programming – the question shifts to who is doing this and how they acquire the necessary tools.
“The relay attack technique is widely known among car thieves, and instructions are readily available online,” Cluley explained. Rogers added, “Car theft equipment is surprisingly easy to obtain. Most car thieves don’t need deep technical knowledge; they operate pre-configured tools, often just pressing a button or waving an antenna.”
The real expertise, Rogers clarified, lies higher up in the criminal supply chain – those who develop and distribute these illicit tools, including OBD2 programmers tailored for theft. Pilton noted that the tools themselves aren’t exclusively designed for car theft. “Relay devices, for instance, are based on legitimate communication technology. Criminals repurpose them, much like a crowbar. The individuals committing the theft might just be operatives using simple, pre-configured devices.”
Reedman emphasized the low skill threshold: “It requires minimal skill. They likely watch online videos and buy relay equipment. It’s trivial, not true ‘hacking’ which demands significant expertise.” Shockingly, reports indicate even children as young as 10 are involved in car theft, highlighting how accessible and easy these methods have become.
Manufacturer Accountability and the Response from Mercedes-Benz
With car theft rising and keyless entry cars being prime targets, the spotlight turns to manufacturers and their responsibility to enhance security. Wright argues, “The automotive industry lags behind many others in protecting against technological attacks.”
I contacted Mercedes-Benz to address concerns about keyless vehicle theft and manufacturer accountability. A spokesperson stated, “The security of our organization, products, and services is a top priority in our R&D.”
My 2018 GLC model predated the security enhancements Mercedes implemented from 2019 onwards.
The spokesperson explained that from mid-2019, the “facelift version of the GLC received a motion sensor in the key. If the key remains still for a period, the KEYLESS GO function deactivates, preventing relay attacks.” My 2018 model, unfortunately, missed this upgrade.
Mercedes also highlighted features like temporary KEYLESS GO deactivation and the Mercedes me service with “stolen vehicle help,” allowing users to report theft and initiate vehicle tracking. However, they didn’t comment on why KEYLESS GO deactivation isn’t more prominently presented to customers at purchase.
The Convenience vs. Security Trade-off and Blame Shifting
Pritchard argues, “Car manufacturers prioritize ease-of-use over security.” He pointed to Range Rover thefts and JLR’s own insurance offering due to unaffordable premiums as evidence of the severity of the problem.
Rogers believes manufacturers lack a deep understanding of the criminal ecosystem and urgency in addressing new theft techniques. “Solutions exist, but there’s a reluctance to admit the problem and act decisively.” He criticized the tendency to blame victims, suggesting owners should take extreme measures like storing keys in specific locations or blocking cars in. “This is wrong – the negligence lies with manufacturers. They are aware of these vulnerabilities, but action is often slow. However, manufacturers are also victims. Stronger international law enforcement is needed to target the criminal tool suppliers.”
Some manufacturers are implementing improvements like motion sensors in key fobs and time-of-flight technology for key proximity verification. However, making customers aware of keyless entry risks at the point of sale is a simple yet often overlooked step.
Pilton emphasizes shared responsibility: “Preventing car theft requires collaboration between manufacturers, software developers, and regulators. Minimum security standards and informed consumer choices are essential.”
The Criminal Justice Bill: A Step Forward, but with Concerns
The UK’s Criminal Justice Bill, introduced in November 2023, aims to criminalize the possession of electronic devices used for vehicle theft. This includes signal jammers and, potentially, OBD2 programming tools used for illegal purposes.
Rogers raises a concern from the security research community: “The Bill could hinder security research, as using these technologies for testing and vulnerability discovery might lead to arrest.” Balancing law enforcement needs with legitimate security research is crucial as the Bill progresses through legislation.
“Dumb Cars” and the Appeal of Low-Risk, High-Reward Theft
Criminals often target the easiest opportunities. Relay attacks and OBD2 programming offer a low-risk, high-reward scenario. No forced entry, no alarms – cars simply vanish silently. “It’s low-risk with high resale value because there’s no damage to the vehicle,” Pritchard explained.
Pilton notes, “While traditional key-based systems have weaknesses, keyless entry introduces new vulnerabilities to specific attack methods.” Cluley, now a “dumb car” owner, reflects the sentiment of many who prioritize security over convenience.
The sheer volume of shared theft experiences online underscores the scale of the problem. Recovery rates are low, and successful prosecutions are even rarer, creating a climate of impunity for car thieves.
The Challenges of Prosecution and Vehicle Recovery
Wright laments the “very poor” prosecution rates for this type of theft. “They’re gone before you notice, tracking disabled, plates changed. The car is likely overseas before the day ends.”
Rogers described efforts to intercept stolen cars in containers or dismantle chop shops, but emphasized that tackling the root issue – the international criminal tool supply chain – is paramount.
Modern car theft often leaves no trace of forced entry, unlike older methods involving broken windows.
Pilton, from his law enforcement experience, highlighted the difficulties in identifying perpetrators. “Investigating these ‘overnight disappearances’ is incredibly challenging. Even locating cars is not always followed by prosecution. Organized crime groups often leave minimal traces at each scene, making direct attribution to specific thefts difficult.” However, law enforcement can build broader cases against these groups through accumulated evidence.
A month after my car was stolen, there’s still no sign of it or the other stolen vehicles. The detective speculated it might have been used for ram-raiding cash machines, given its size. It could be anywhere now – overseas, in a chop shop. The investigation continues, including forensic analysis and tracking data, but recovery is unlikely.
Securing Your Keyless Car: Practical Steps
On the night of the theft, my key was in a drawer at the back of the house, a naive attempt at security. I wasn’t sufficiently aware of relay attacks. Now, my perspective is drastically changed.
The consistent advice from experts for protecting keyless cars? Faraday protection. “Use a Faraday box or wallet to block key signals at home,” Cluley advises. “Always store keys in it when you’re home, including spare keys.”
Reedman recommends testing Faraday effectiveness: “Try unlocking your car with the key in the Faraday box. If it works, it’s not effective enough.” He emphasizes fully enclosed metal boxes for reliable signal blocking.
Other recommendations include: storing keys far from doors, disabling keyless ignition if possible, using mechanical steering locks, and OBD2 port locks. Rogers suggests OBD2 port locks as a deterrent, making unauthorized access more difficult.
Just before publishing, Dan Bulman from KEYSHIELD contacted me about their device – a sleeve that disables the key fob battery when stationary using motion sensor technology, aiming to prevent relay and cloning attacks. I tested it on my new car, but it seemed overly effective, preventing even legitimate key access and triggering the alarm. Further investigation is needed to assess its compatibility.
For my new car, I’m adopting a “belt and braces” approach: Faraday box and steering wheel lock. Cynicism, in this context, is a valuable security tool.
Until car manufacturers fully address keyless system vulnerabilities and educate owners, awareness is crucial. Articles like this aim to empower car owners with knowledge to protect themselves against these evolving theft methods, particularly the risks associated with keyless ignition and the potential misuse of OBD2 tools.